Check Point’s Most Wanted Malware report for December 2018 demonstrates that cryptocurrency mining malware was the principal malware danger in December. The top four malware dangers in December 2018 were all cryptocurrency miners.
Continue reading “Cryptocurrency Mining Malware Tops Most Wanted Malware List”Category: Cybersecurity Alerts
The Cybersecurity Alerts section provides timely notifications about emerging cyber threats, vulnerabilities, and potential risks that organizations must be aware of. This section offers critical updates on newly identified malware, software vulnerabilities, and security breaches, enabling businesses and compliance teams to take proactive measures to safeguard their networks and data. Staying informed with real-time alerts is essential for maintaining a strong security posture in an ever-evolving threat landscape.
773 Million Electronic mail Addresses and 21 Million Unique Passwords Listed for Sale
A huge collection of login identifications that contains roughly 773 million electronic mail addresses has been uncovered by safety researcher Troy Hunt. Hunt is an Australian Microsoft Regional Director and keeps the Have I Been Pwned (HIBP) website, where people can test to see whether their login identifications have been thieved in a data breach.
Continue reading “773 Million Electronic mail Addresses and 21 Million Unique Passwords Listed for Sale”Highly Sophisticated Apple Vishing Scam Identified
A sophisticated Apple vishing cheat has been exposed. Contrary to most phishing attempts that use electronic mail, this cheat used voice calls (vishing) with the calls seeming to have come from Apple.
Continue reading “Highly Sophisticated Apple Vishing Scam Identified”January 2019 Patch Tuesday Updates
January 2019 Patch Tuesday has seen 51 flaws rectified in Microsoft products. There are four updates to rectify mistakes in the Microsoft Edge Browser. Seven of the 51 updates have been shown as crucial.
Continue reading “January 2019 Patch Tuesday Updates”NIST Issues Draft Paper on Telehealth and Remote Monitoring Device Cybersecurity
The National Institute of Standards and Technology’s National Cybersecurity Center of Excellence (NCCoE) has issued a draft paper covering the secrecy and safety dangers of telehealth and distant checking appliances together with best practices for safeguarding the telehealth and distant checking ecosystem.
Continue reading “NIST Issues Draft Paper on Telehealth and Remote Monitoring Device Cybersecurity”Adobe Patches Actively Abused 0-Day Vulnerability in Flash Player
On Wednesday, December 5, 2018, Adobe released an update to rectify a vulnerability in Adobe Flash Player that is being leveraged by a threat group in targeted attacks in Russia. The threat group has previously attacked a healthcare service in Russia that is used by senior civil servants.
Continue reading “Adobe Patches Actively Abused 0-Day Vulnerability in Flash Player”Spotify Phishing Scam Identified: User Accounts Breached
Scientists at AppRiver have noticed a Spotify phishing cheat that tries to get users to disclose their Spotify identifications. The electronic mails use brand imaging that makes the electronic mails seem to have been transmitted by the music streaming facility. The emails are genuine, even though there are indications that the messages are not genuine.
The electronic mail template used in the Spotify phishing cheat asserts the user requires to verify their account details to get rid of limitations and make sure they can carry on to use their account. The messages contain the Spotify symbol and contact information in the footer. The electronic mails have a link that account holders are requested to click to take them to the Spotify website where they are requested to enter in their account identifications.
The Spotify phishing scam doesn’t contain a spoofed sender electronic mail address which makes this cheat quite easy to identify. Spotify is mentioned in the electronic mail address, but the domain makes it clear that the electronic mail has not come from a domain used by Spotify. That said, a lot of electronic mail receivers might fail to check the sender name and might click the link and be directed to the phishing web page.
The phishing web page used to gather account identifications also has Spotify branding and seems to be almost identical to the genuine Spotify login page. The only indication that the website is not genuine is the URL.
The information gathered through this phishing cheat might let the attacker gain control of a user’s account. The password to the site will be gotten, which might be used to gain access to other accounts maintained by the sufferer if the password has been reused on other websites. Passwords can also disclose other information concerning an individual, such as their dates of birth, and can provide hints as to how their passwords are produced. That can make brute force attacks on other websites much easier and faster to perform.
California Wildfire-Themed BEC Attack Identified
It’s usual for phishers to use natural catastrophes as a lure to get ‘donations’ to line their pouches instead of helping the sufferers and the California wildfires are no exception. A lot of people have lost their lives in the fires and the death toll is likely to increase further as hundreds of people are still unaccounted for.
Entire towns such as Paradise have been completely devastated by the wildfires and hundreds of people have lost their homes. Numerous are suffering, have nowhere to reside, and have lost everything. As expected many people desire to donate money to assist the sufferers rebuild their lives. The attackers are using the sympathy of others to deceive companies.
A California wildfire phishing cheat was recently noticed by Agari that tries to capitalize on the tragedy. Nevertheless, contrary to several similar phishing campaigns that depend on huge volumes of electronic mails, this campaign is much more targeted.
The scammer is carrying out a business electronic mail compromise attack using the electronic mail account – or a deceived account – of the CEO of a firm. The first phase of the scam involves a rapid electronic mail to a worker questioning if they are available to assist. When a response is received, a second electronic mail is sent asking the worker to make a purchase of 4 Google Play gift cards, each of $500.
The CEO asks if there is a local store where the cards can be bought and asks the worker to make the purchase ASAP and to scratch off the reverse side, get the codes, and email them back. The electronic mail claims the CEO requires the cards to send to customers who have been caught up in the wildfires to provide help.
While the selected method of sending help is doubtful, to say the least, and the electronic mails have grammatical and spelling mistakes, the use of the CEO’s electronic mail account may persuade workers to go ahead as ordered. These cheats work because workers do not want to ask their CEO and desire to reply swiftly. Even though a request may be strange, the reasoning behind the request seems perfectly genuine.
Although this might seem like an obvious fraud, at least worthy of a call or text to the CEO to confirm its validity, some workers will no doubt not question the request. Each one that does as trained will cost the company $2,000.
This kind of cheat is common. They are often associated with wire transfer requests. In the rush to reply to the CEO’s request, a transfer is made, which might be for tens of thousands of dollars. The worker replies to the message through electronic mail saying the transfer has been made, the scammer erases the electronic mail, and the fake transfer is often not detected until after the scammer has used money mules to withdraw the money from the account.
Access to the CEO’s electronic mail account can be obtained in several ways, even though a spear phishing attack is common. Spam filtering solutions can assist to decrease the possibility for the first attack to take place and two-factor verification controls can avoid account access if identifications are stolen.
Staff training is vital to increase awareness of the danger of BEC attacks. Policies must also be applied that need all transfer requests sent through electronic mail, and any out-of-bounds requests, to be confirmed over the phone or through a text before a transfer is made.
Cofense Expands 24/7 Global Phishing Defense
The Cofense Phishing Defense Center (PDC) was introduced to ease the load on IT safety teams by letting them offload some of the load of searching through electronic mails informed by their end users and analyzing those electronic mails to identify the actual threats.
When workers report doubtful electronic mails – through
The Phishing Defense Service saves companies a substantial amount of time and effort and lets dangers to be identified and alleviated much more quickly. With the volume of phishing dangers rising, occurrence responders can easily get caught up identifying dangers in the hundreds of electronic mails that are informed as ‘suspicious’ by their workers. Data from
The Cofense PDC team already works round-the-clock to evaluate active phishing dangers, nevertheless, the growth of the facility makes sure that irrespective of the time of day or night, new dangers are recognized in the shortest possible time frame. This is particularly vital for firms that have offices in several countries and time zones. Those businesses must not have to wait until business hours for dangers to be identified. They need to be identified day or night.
“Since threat actors do not sleep, neither should your defense capabilities,” clarified Josh Nicholson, Senior VP of Professional Services at Cofense. “Our improved, round-the-clock phishing defense facility puts clients at ease by offering expert analysis and reaction for any informed doubtful electronic mail, any day, any time, in a matter of minutes.”
The expansion will make sure that malware experts are always on hand to evaluate informed phishing attempts and assist clients to alleviate new phishing attempts much more quickly.
United States Leads the World as Primary Host of Malware C2 Infrastructure
The United States is home to the maximum proportion of malware command and control (C2) infrastructure – 35% of the international total, as per fresh research circulated by phishing defense and threat intelligence company Cofense. 27% of network Indicators of Compromise (IoCs) from phishing-borne malware are also either situated in or proxied through the United States. Cofense data indicate that Russia is in the second position with 11%, followed by the Netherlands and Germany with 5% each and Canada with 3%.
C2 infrastructure is utilized by hackers to communicate with malware-infected hosts and deliver orders, download new malware modules, and exfiltrate data.
Threat actors are more concerned with locating somewhere to find their C2 infrastructure to minimize risk instead of locating it in a particular country. Cofense notices that “C2 infrastructure is extremely prejudiced toward compromised hosts, showing a high occurrence of host compromises inside the United States.” That obviously makes perfect sense, since there are more possible hosts to compromise in the United States than in other nations.
“Some companies will obstruct any links coming from nations known for the origination of malevolent activity that they don’t do business with,” clarified Darrel Rendell, the principal intelligence expert at Cofense. That would make hosting C2 infrastructure in the United States beneficial, as links between malware and those servers would be less likely to raise red flags.
In a latest blog post, Cofense provides instances of the distribution of C2 infrastructure using two usual banking Trojans: TrickBot and Geodo. Both banking Trojans are widely used in attacks on Western nations, and attacks have risen in frequency in 2018. The two Trojans are conspicuously different because they belong to different malware families and are used by different threat actors.
In both instances, the infrastructure is growing and the C2 sites are highly different, even though data demonstrate very different distributions of C2 infrastructure for each malware variation. TrickBot’s main site for its C2 infrastructure is Russia, followed by the U.S. Geodo on the other hand mainly uses the U.S, followed by the Germany, France and the United Kingdom, with next to nothing situated in Russia.
Cofense clarifies that the widespread and widely distributed C2 infrastructure will not only assist to make sure these two threats remain active for longer but also that using geolocation to distinguish genuine and malevolent traffic might not be particularly effective.
Zero-Day Windows Task Scheduler Vulnerability Exploited by Threat Group
On August 27, a safety scientist with the online moniker SandboxEscaper found a zero-day weakness in Windows Task Scheduler (Windows 7-10) and issued a proof-of-concept exploit for the fault on GitHub. Microsoft was not alerted to the fault and was not given time to issue a solution to avoid the fault from being abused.
Obviously, the exploit is now being used by at least one hacking group to attack companies. Cybersecurity company ESET reports that a new threat group named PowerPool has been carrying out targeted attacks using the backdoor.
The fault is present in the Advanced Local Procedure Call (ALPC) of Windows Task Scheduler. If local access to an appliance is gained, it is possible to elevate rights to SYSTEM level by overwriting certain files which are not safeguarded by filesystem access control lists.
Microsoft has not yet rectified the fault – and will likely not do so until Patch Tuesday on September 11 – even though Acros Security has issued a micropatch that will block the fault from being abused. Even though the micropatch has been available for numerous days, many companies have decided to wait until Microsoft solves the problem and remain susceptible to attack.
ESET telemetry data indicates the PowePool group has already carried out attacks using a tad altered type of the proof-of-concept exploit, which was recompiled from the source code published on GitHub. Attacks have been noticed in the US, Russia, India, Ukraine, Chile, Poland, Germany, UK, and the Philippines.
In the assaults, the group uses the exploit to overwrite C:\Program Files(x86)\Google\Update\GoogleUpdate.exe to give its malware important consents on systems. According to a latest ESET report, the first stage of the attack involves offering the malware through electronic mail in a spam campaign that utilizes Symbolic Link (.slk) file attachments. The spam electronic mails are part of a targeted spear-phishing campaign, with the electronic mail attachment disguised as an invoice.
The first phase of the malware is used for reconnaissance to identify systems of interest that are worthy of a more wide-ranging compromise. If the system is of interest, the malware downloads an added module that is capable of carrying out commands on a compromised system, can download more files, upload data to the attacker’s C2 server, and can halt processes running on an infected appliance.
ESET notes that the second phase of the malware downloads a range of genuine tools which support the attackers to move laterally on the network and compromise additional appliances.
The published exploit has now been included in the attackers’ arsenal and is being utilized to increase privileges on a compromised system. The exploit was utilized within 48 hours of it being circulated on GitHub. This is a typical example of what occurs when details of vulnerabilities are disclosed outside a coordinated disclosure procedure.
Micropatch Obstructs Zero-Day Vulnerability in Windows Task Scheduler
On August 29, 2018, a proof-of-concept use for a zero-day vulnerability in Windows Task Scheduler was published on GitHub by a safety researcher.
The vulnerability had not earlier been disclosed to Microsoft, and therefore, no repair has been released to tackle the fault. If misused, a malevolent actor might elevate consents of malevolent code running on a compromised appliance from guest or user level to administrator level with complete system access.
The fault is not likely to be tackled by Microsoft before September Patch, even though the cybersecurity company Acros Security has created a workaround – a micropatch – that avoids the abuse of the vulnerability. The repair will safeguard weak 64-bit Windows types until Microsoft issues a repair to rectify the fault.
The abuse for the zero-day vulnerability in Windows Task Scheduler was only verified to work on 64-bit types of Windows. Nevertheless, two safety scientists proposed the abuse might be tweaked to work on 32-bit Windows types. Those tweaks are comparatively minor. 32-bit Windows types are therefore also weak and will likely remain so until Microsoft tackles the problem.
The micropatch was made available for 64-bit Windows 10 v1803 types on August 30, 2018 with a micropatch for Windows Server 2016 released the next day together with detailed information regarding how the repair avoids the vulnerability from being abused. The source code has also been released.
Businesses need to connect the micropatch through the opatch Agent client. By providing the source code, businesses are able to apply the repair to their systems without using the opatch agent.
Even though the zero-day has been publicly available for many days, there are no reports of the vulnerability being used by threat actors in the wild. Nevertheless, that is not likely to remain the case for long. It is therefore strongly
New Crucial Apache Struts Vulnerability Found
A new Apache Struts vulnerability has been found in the main functionality of Apache Struts. This is a serious vulnerability that lets distant code execution in certain configurations of the framework. The vulnerability might prove more serious than the one that was abused in the Experian hack in 2017.
Apache Struts is an open source framework utilized in several Java-based web applications. It has been approximated that at least 65% of Fortune 500 firms use Struts to some extent in their web applications.
The vulnerability was known by safety scientist Man Yue Mo of Semmle and is being followed as CVE-2018-11776. Semmle unveiled the vulnerability to the Apache Foundation and the timing of publication of the vulnerability matches with the release of a patch to repair the vulnerability.
The possibility for abuse is limited by the fact that only certain configurations of Apache Struts are susceptible to attack. While these configurations are not likely to be set by the bulk of companies, they are far from unusual.
The Apache Foundation has released particulars of the configurations that are susceptible:
- When the alwaysSelectFullNamespace flag is set to true, which is the default configuration using the Struts Convention plug-in.
- When the Struts configuration file of an application has “a <action …> tag that does not identify the optional namespace attribute or specifies a wildcard namespace (e.g. “/*”)”.
Now that the vulnerability has been unveiled it is necessary for all companies to update vulnerable versions of Struts as a priority. The vulnerability is present in all supported versions of Apache Struts 2. Users of Struts 2.3 have been advised to upgrade to 2.3.35 and users of 2.5 must upgrade to 2.5.17.
As Semmle noted in an August 22 blog post, earlier vulnerabilities in Apache Struts have led to exploits being developed within a day of the announcement being made of a vulnerability.
It is possible that targets can be easily identified and attacks are unavoidable. As the Experian hack indicated, the failure to tackle Struts weaknesses can prove extremely damaging.
Necurs Botnet Now Dispersing Marap Malware
The Necurs botnet is being utilized to transmit huge quantities of spam electronic mails having Marap malware. Marap malware is presently being utilized for reconnaissance and learning about sufferers. The aim seems to be the creation of a system of infected users that can be targeted
The malware generates an exclusive impression for each infected appliance, contacts its C2 server, and transmits information concerning the sufferer’s system to the attackers including username, operating system, language, country, IP address, domain name, hostname, installed anti-virus software, and details of Microsoft Outlook OST files.
The malware has some basic anti-analysis characteristics and can find when it has been installed on a virtual machine and contains measures to obstruct debugging and sandboxing.
Marap malware is modular and can easily be updated with additional modules post-infection to provide increased functionality. It helps as a malware dropper that can be used to provide many different payloads, even though it is presently unclear what those payloads will be.
The malspam campaign was discovered by safety scientists at Proofpoint who say it involves millions of emails. Marap malware is delivered using a range of different electronic mail attachments, with Microsoft Excel Web Query files (IQY) preferred. The messages have iqy files as attachments, or they are incorporated in PDF files and password-protected ZIP files. Standard Microsoft Word documents with malevolent macros are also being transmitted.
The spam campaign includes a range of different electronic mail subjects and messages including sales requests, important banking documents, invoices, and simple electronic mails just containing malevolent PDF files and ZIP file attachments.
Proofpoint notes that there has been a surge in these flexible malware variations in recent months as threat actors move away from ransomware and ‘noisy’ malware that are easy to notice. In its place, downloaders, for example, Marap malware gives attackers the flexibility to introduce a variety of different attacks and carry out a recce to identify systems that deserve a more significant compromise.
FTC Issues Warning Concerning New Netflix Phishing Scam
The U.S. Federal Trade Commission has circulated a warning about a new international Netflix phishing cheat that tries to deceive Netflix subscribers into revealing their account identifications and payment information. The cheat uses a tried and tested method to get that information: The warning of account closure because of payment information being out of date.
Users are transmitted a message requesting them to update their payment details since Netflix has experienced difficulties getting the monthly subscription payment. The user is provided with an “Update Account Now” button which they can click to insert their accurate banking/card information. Nevertheless, clicking the link will not guide the user to the official Netflix site, instead, they will be taken to a web page on a site operated by the scammer. On that site, Netflix login identifications will be harvested together with the banking information entered by subscribers.
The latest campaign was recognized by the Ohio Police Division, which shared a copy of the phishing electronic mail on Twitter. The FTC also issued a warning about the new Netflix phishing cheat in the latest blog post.
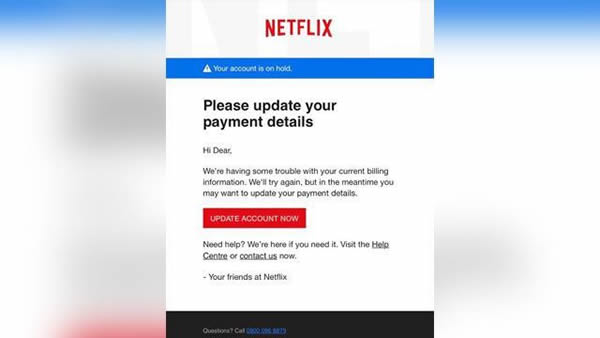
Image Source: Ohio Police via FTC
As you can see from the picture, the message appears official as it has the Netflix logo and color scheme. The message also strongly looks like official electronic mail communications often sent by Netflix. Nevertheless, there are tell-tale indications that the electronic mail is not what it appears. Netflix is naturally conscious who their subscribers are and addresses electronic mails to users by their first name. In this electronic mail, the message starts with “Hi Dear.”
Less visible is the hyperlink, however it is something that is fairly easy to check by hovering the mouse arrow over the button. That will show the actual URL, which is not the official Netflix website. One more indication is the phone number on the electronic mail is a U.S. number, which for any person based in another country would be extremely doubtful.
If the link is clicked, the page the user is directed to appears official and is nearly indistinguishable from the actual site, even though if a user checks the URL it will verify they are not on the actual Netflix site for their country.
All of these warning indications must be identified by users, but several people fail to cautiously check messages before clicking. To avoid phishing cheats such as this, make certain you carefully check all electronic mail messages before replying and if ever you receive an electronic mail containing any warning, visit the authorized URL for the firm directly by entering in the website directly into the browser instead of clicking a link in an electronic mail.
Orange Livebox Modems Revealing WiFi Information
Hackers are abusing a fault (CVE-2018-20377) in Orange Livebox ASDL modems that let them get the SSID and the Wi-Fi password of the appliances in plaintext. As soon as access is gained to a weak modem, attackers could update the firmware and alter device settings. Abusing the vulnerability is as easy as sending a GET request.
The vulnerability was identified by Troy Mursch at Bad Packets, who noted the company’s honeypots were being scanned with
Identifying the appliances is a swift and easy procedure. A search can be carried out on the search engine Shodan. A rapid search by Mursch demonstrated there are presently 19,490 of the vulnerable modems in use. Additional 2,018 modems were not leaking data but were exposed to the Internet.
As soon as identified, an attacker only requires to send a GET request to “/get_getnetworkconf.cgi to get plaintext SSIDs and WiFi passwords. An attacker can also see the phone number of the client and the MAC addresses and names of all related clients. Mursch also found that password reuse was widespread, and many appliances had not set a custom password, instead, they used the default admin/admin identifications.
The attack identified by Mursch seems to come from within Spain from a Telefonica Spain customer. It is presently unclear why attempts are being made to access the modems’ Wi-Fi identifications.
Mursch has reported the fault to CCN-CERT, Orange Espana, and Orange-CERT and the vulnerability is presently being probed. The
BleedingBit Vulnerabilities Affect Millions of Wireless Access Points
Cisco, Meraki, and Aruba provide no less than 70% of business wireless access points, which places all of those companies at risk. It is not yet known precisely how many appliances are vulnerable and have the BleedingBit vulnerabilities, even though Armis Labs doubts millions of appliances might be affected.
If theBleedingBit vulnerabilities are abused, attackers would be able to take complete control of the access points without any requirement for verification. The access points could be deactivated, data could be interrupted, malware fitted, or the attackers might use the vulnerabilities to gain access to company systems served by the access points and access any appliance in the neighborhood of the AP.
TwoBleedingBit vulnerabilities have been found. CVE-2018-16986 lets memory corruption in the BLE stack, through which complete control of the AP might be gained. To abuse the vulnerability, an attacker would need to be within the limit of the AP and BLEwould need to be turned on. No knowledge of the appliance would be needed and there are no other preconditions to abuse the vulnerability.
An attacker would need to send particularly created packets to the AP containing code which is run in the next phase of the attack. The second phase involves sending an overflow packet to trigger a vital memory overflow which lets the attacker run the earlier sent code.
The vulnerability
The second of the BleedingBit vulnerabilities – CVE-2018-7080 – is existing in the over-the-air firmware download (OAD) feature of Texas instruments’ chips utilized in ArubaSeries 300 Wi-Fi Access Points. The vulnerability is a development backdoor tool that has not been detached. If abused, the vulnerability would let a new and completely different variety of firmware to be installed, letting the attacker gain complete control of the appliance.
Armis Labs says that abuse of the BleedingBit vulnerabilities would not be spotted by usual AV solutions and would be unlikely to raise any red flags. The attacker might move laterally between network parts, interrupt traffic, install malware, interfere with operating systems, and hijack a wide variety of appliances unnoticed.
Cisco has already repaired its affected appliances, and Meraki has published help on how users can make modifications to BLE settings to avoid misuse of the vulnerabilities. Misuse of CVE-2018-7080 can be obstructed by deactivating OAD functionality. Texas Instruments has now rectified the fault in BLE-STACK v2.2.2.
Zero-Day VirtualBox Vulnerability and Exploit Published
Particulars of a zero-day VirtualBox vulnerability have been published online together with a step by step activity.
The vulnerability in the Oracle open source hosted hypervisor was published on GitHub by Russian safety scientist, Sergey Zelenyuk, instead of being disclosed to Oracle to permit the bug to be repaired. The decision was affected by an earlier
Zelenyuk described the decision to go public with the vulnerability and exploit was because of frustration with Oracle and the bug revelation and bug bounty procedure – “I like VirtualBox and it has nothing to do with why I publish a 0day vulnerability. The purpose is my disagreement with
The vulnerability is a series of bugs that can be abused to allow malevolent code to dodge the virtual machine and perform on the original operating system. The exploit activates a buffer surplus situation using packet descriptors which allow malevolent code to be run in kernel ring 3, which is used for most user programs. It is possible to merge the exploit with kernel privilege growth bugs to gain access to kernel ring 0.
As per Zelenyuk, the exploit is 100% dependable and works irrespective of the host or original operating system and affects all VirtualBox releases.
The vulnerability is specifically disturbing for malware scientists as VirtualBox is a popular selection for studying and reverse engineering malware in a secure atmosphere. If malware authors were to insert the exploit into their malware, it would be possible to flee the VM and infect the safety researcher’s machine.
It remains to be seen how swiftly VirtualBox will be repaired. With the vulnerability and abuse now in the public domain, it is possible that Oracle will not wait 15 months to create a repair.
WordPress GDPR Compliance Plugin Vulnerability Being Actively Abused
Websites with the WordPress GDPR Compliance plugin fitted are being hijacked by hackers. A vulnerability in the plugin is being abused, allowing attackers to change site settings and record new user accounts with admin rights.
The vulnerability can be distantly abused by unauthorized users, a lot of whom have automated misuse of the vulnerability to hijack as many sites as possible prior to the vulnerability is rectified.
The vulnerability was found by safety scientists at Defiant, who noted that in a number of attacks, after abusing the vulnerability the attackers have rectified
Compromised websites can be utilized for phishing and other cheats, or the sites might have exploited kits uploaded to silently downloaded malware onto visitors’ appliances. An examination of compromised websites has not exposed any payload at this phase. Defiant scientists propose that the initial goal is to compromise as many sites as possible before the
vulnerability weakness is rectified. Compromised sites might be sold or the attackers could be biding their time before the attack stage is launched.
After WordPress became aware that the WordPress GDPR Compliance plugin vulnerability was being actively abused in the wild, the plugin was removed from the official WordPress store and the developer was informed. A new type of
Any website proprietor that has the WordPress GDPR Compliance plugin installed should make sure it is updated to version 1.4.3, which was released on November 7, 2018. Site proprietors must also check their sites for any indication of illegal modifications and checks must be carried out to see if any new admin accounts have been produced.
Microsoft Patches 12 Critical Vulnerabilities on November Patch Tuesday
Microsoft has released repairs for 12 dangerous vulnerabilities in November Patch Tuesday and has repaired a vulnerability that is being actively abused by at least one threat group. In total, 64 vulnerabilities have been repaired across Windows, IE, Edge, and other Microsoft products.
The 12 dangerous vulnerabilities might let hackers carry out a malevolent code and take complete control of a vulnerable appliance. The bulk of the dangerous vulnerabilities are in the Chakra Scripting Engine, which
CVE-2018-8541, CVE-2018-8542, CVE-2018-8543, CVE-2018-8551, CVE-2018-8555, CVE-2018-8556, CVE-2018-8557, and CVE-2018-8588, are all memory corruption vulnerabilities regarding how the Chakra Scripting Engine controls items in the memory in Microsoft Edge. All eight vulnerabilities might be abused if a user visits a particularly created webpage using the Microsoft Edge browser. The vulnerabilities might also be abused through malvertising.
The other dangerous vulnerabilities are listed below:
CVE-2018-8476 concerns how matters in the memory are controlled by Windows Deployment Services TFTP Server. Misuse of the vulnerabilities would let a hacker perform arbitrary code on a vulnerable server with elevated authorizations.
CVE-2018-8544 concerns how matters in the memory are controlled by Windows VBScript Engine. If abused, an attacker could implement arbitrary code with the same level of rights as the present user. If the user has administrative privileges, an attacker could take complete control of a vulnerable system. The vulnerability could be abused through an inserted Active X control in a Microsoft Office file that hosts the IE rendering engine, through malvertising, or specifically created webpages.
CVE-2018-8553 concerns how items in the memory are controlled by Microsoft Graphics Components. Misuse of the vulnerability would require a user to open a specifically created file, for example, one sent in a phishing electronic mail.
CVE-2018-8609 is the failure of Microsoft Dynamics 365 (on-premises) version 8 to clean web requests to a Dynamics server. If abused, an attacker might run arbitrary code in the context of an SQL service. The fault might be abused by sending a specifically created request to an unpatched Dynamics server.
Microsoft also released a patch for the actively abused Windows Win32k Elevation of Privilege Vulnerability CVE-2018-8589. If abused, an attacker might run arbitrary code in the safety setting of the local system. Nevertheless, system access would first need to be gained before the vulnerability might be abused.
Adobe has also released patches this patch Tuesday for Flash Player, Acrobat, Reader, and Photoshop CC.
